So many documents, so many types of control, but what do all those terms really mean
To begin with, we distinguish between checking the data obtained and checking the identity documents themselves.
RELATED DATA
data that an ID Scanner collects from the identity document.
THE DOCUMENT ITSELF
the source of the data; the identity document
Important to know: The verification of data obtained by the ID Scanner, does not always say anything about the authenticity of the source of that data (the offered document).
Team at RestPort Technologies
Validity check Check whether the identity document has expired.
Validity check compares the expiration date of the identity document read by the ID Scanner with the current date.
After checking, one knows:
- Whether or not the identity document is expired at the time of scanning.
MRZ check Checking the readable MRZ on the identity document.
The MRZ on the identity document consists of 2 or 3 lines of OCR text. Each line contains several elements containing information about the holder or the identity document. Some of these elements, as well as the entire MRZ, are followed by a control number.
These control numbers are a "checksum" over the previous data. A weighted computational test over the numbers that results in an outcome. The software verifies that the check numbers match the rest of the data in the MRZ.
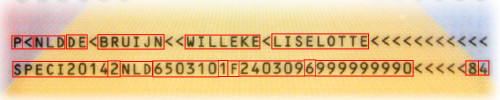
After checking, one knows:
- is the MRZ data correctly read from the identity document.
- or the MRZ data on the identity document may have changed.
RFID chip verification Verification of the data on the chip in the identity document.
Control of the data on an RFID chip has several levels:
BASIC ACCESS CONTROL (BAC)
The ID-Scanner creates a temporary encryption key from part of the MRZ information. Then the ID-Scanner and the chip, via a challenge/response agree on a communication encryption key for this readout session.
PASSIVE AUTHENTICATION (PA)
A list of hashes and a hash algorithm is stored on the chip. This is signed with a digital signature. For each data group, the desired hash can be recalculated and compared with the hash present on the chip.
ACTIVE AUTHENTICATION (AA)
This mechanism uses a challenge-response protocol based on asymmetric cryptography. During inspection, the chip uses its (unpredictable) private key to sign a random bit string chosen by the inspection system. The inspection system verifies the signature with the public key read from the chip. The authenticity of the public key is protected by passive authentication.
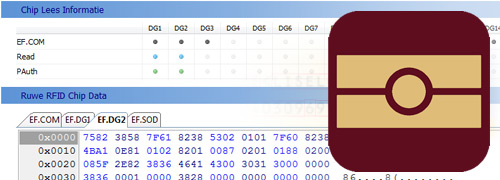
After checking, one knows:
- BAC - The original MRZ data could be used to successfully connect to the chip an agree on an encryption key for communication.
- PA - The integrity of the data in the data groups is guaranteed against the hashes stored in the chip about that data Caution! this does not protect against cloned forgeries where both the data groups and the stored hashes are both properly forged.
- AA - The chip is not cloned; the hidden private key is proven correct by execution of the successful challenge response.